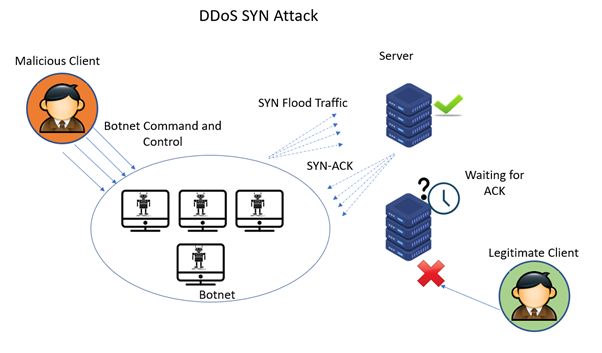
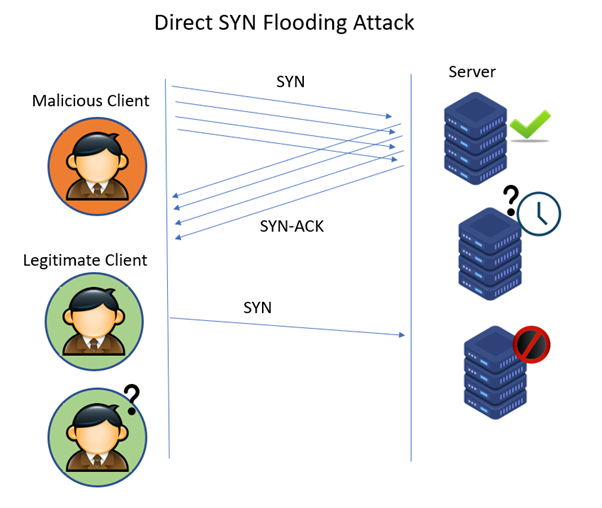
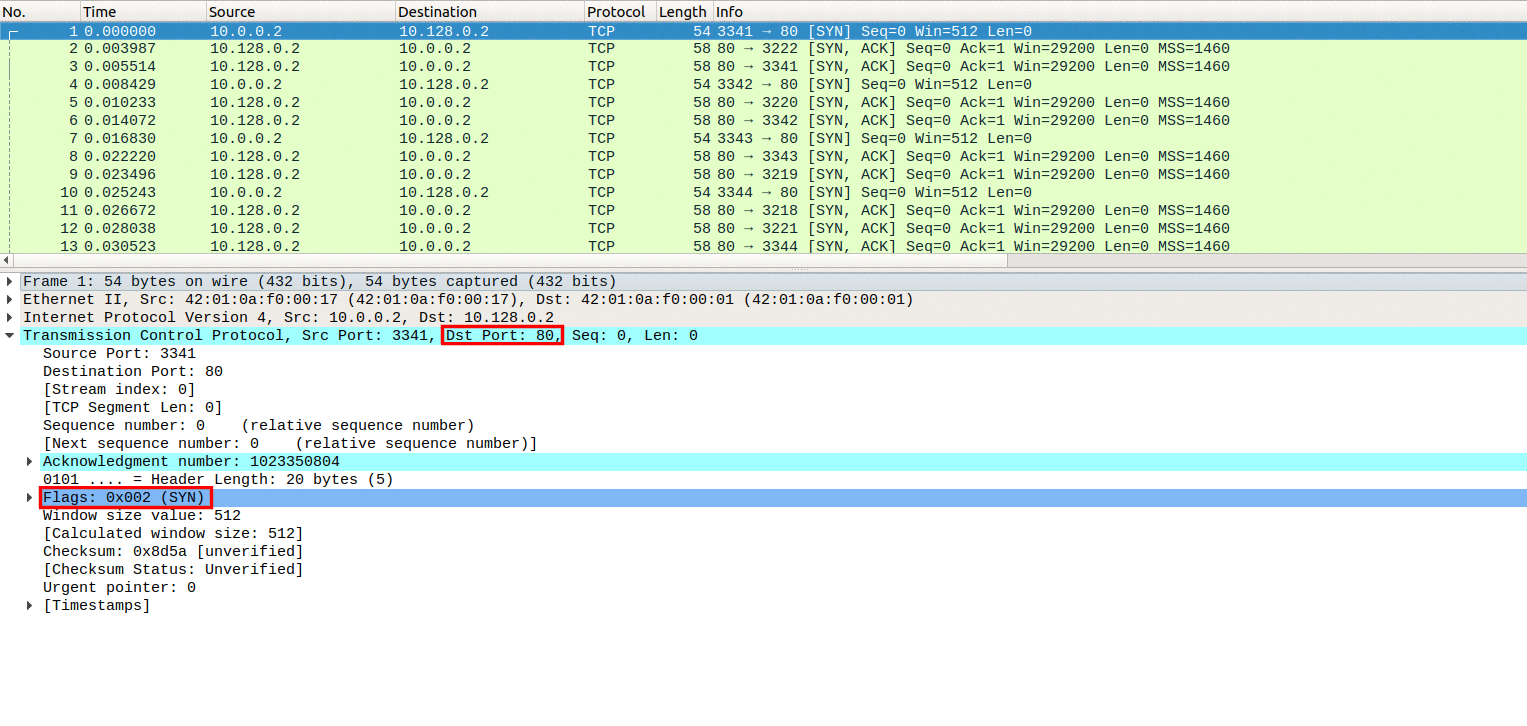
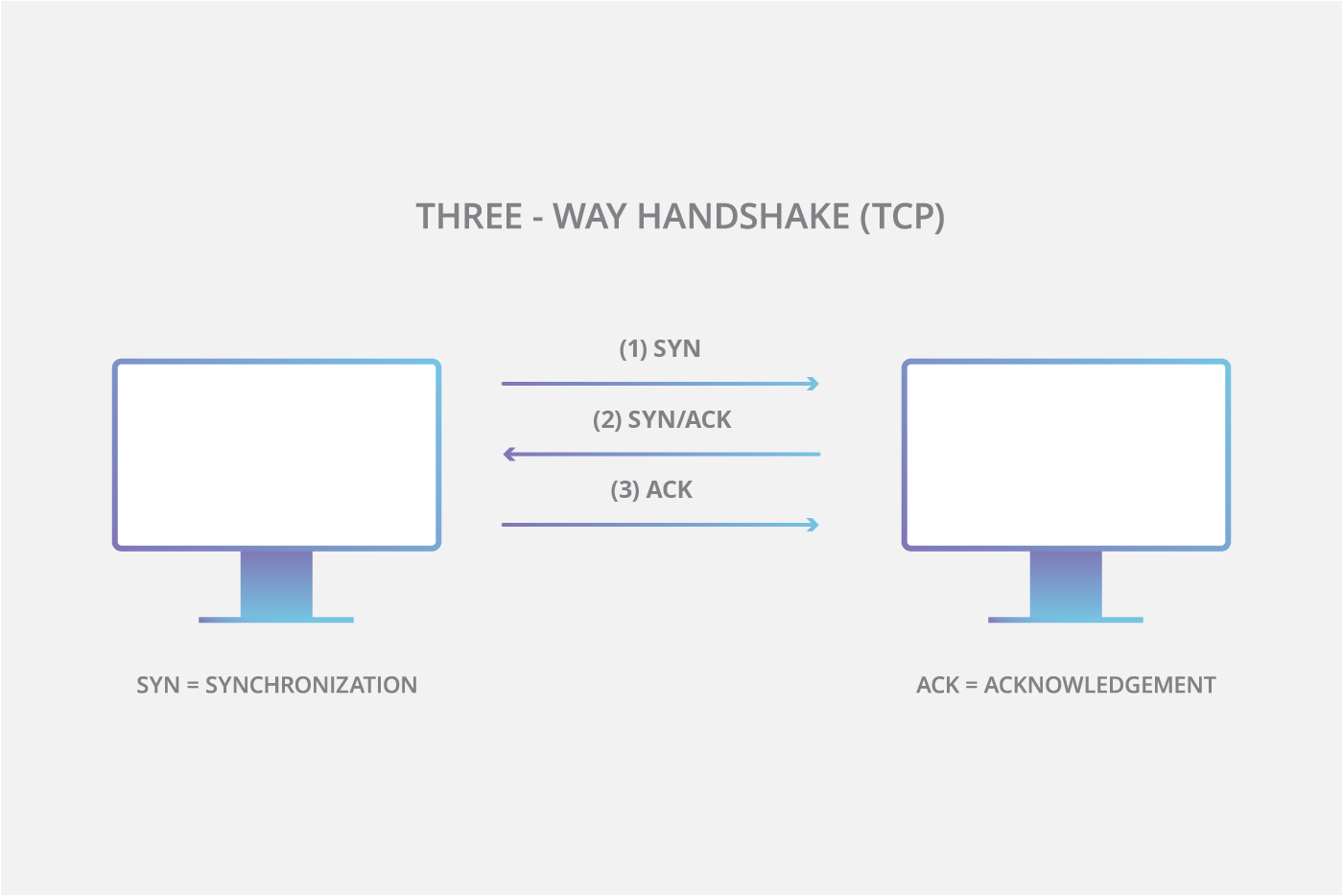
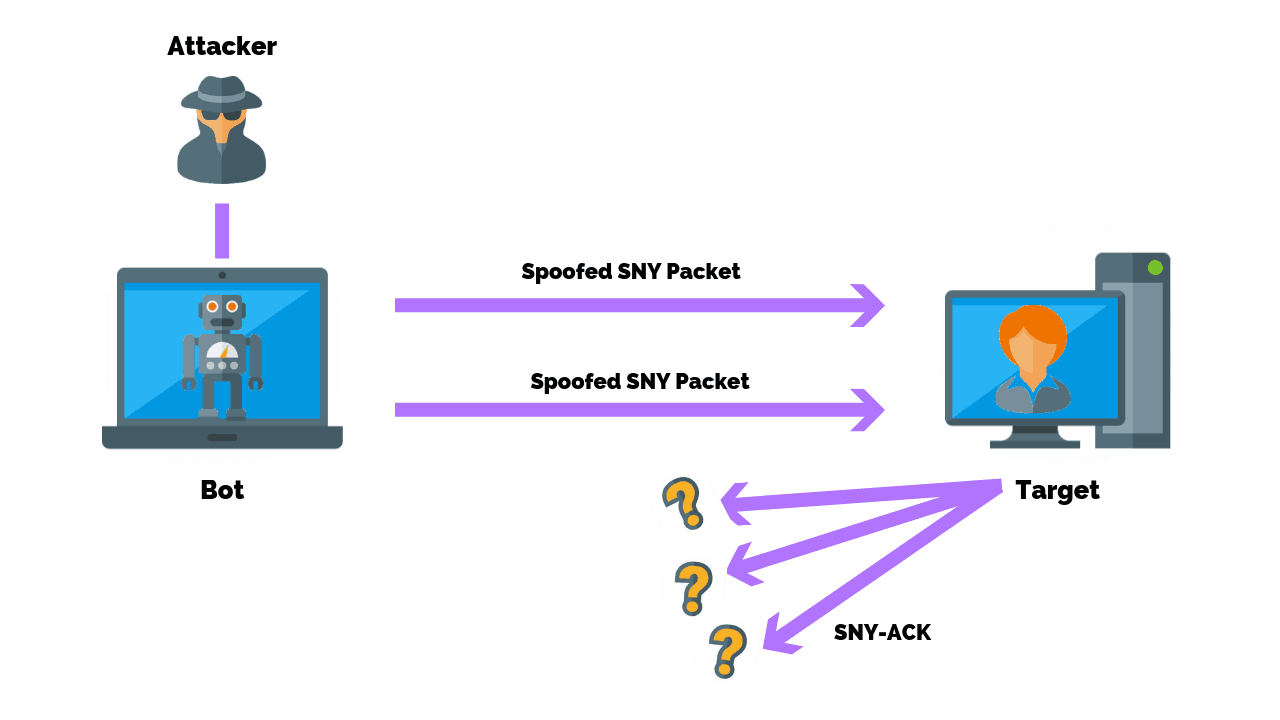
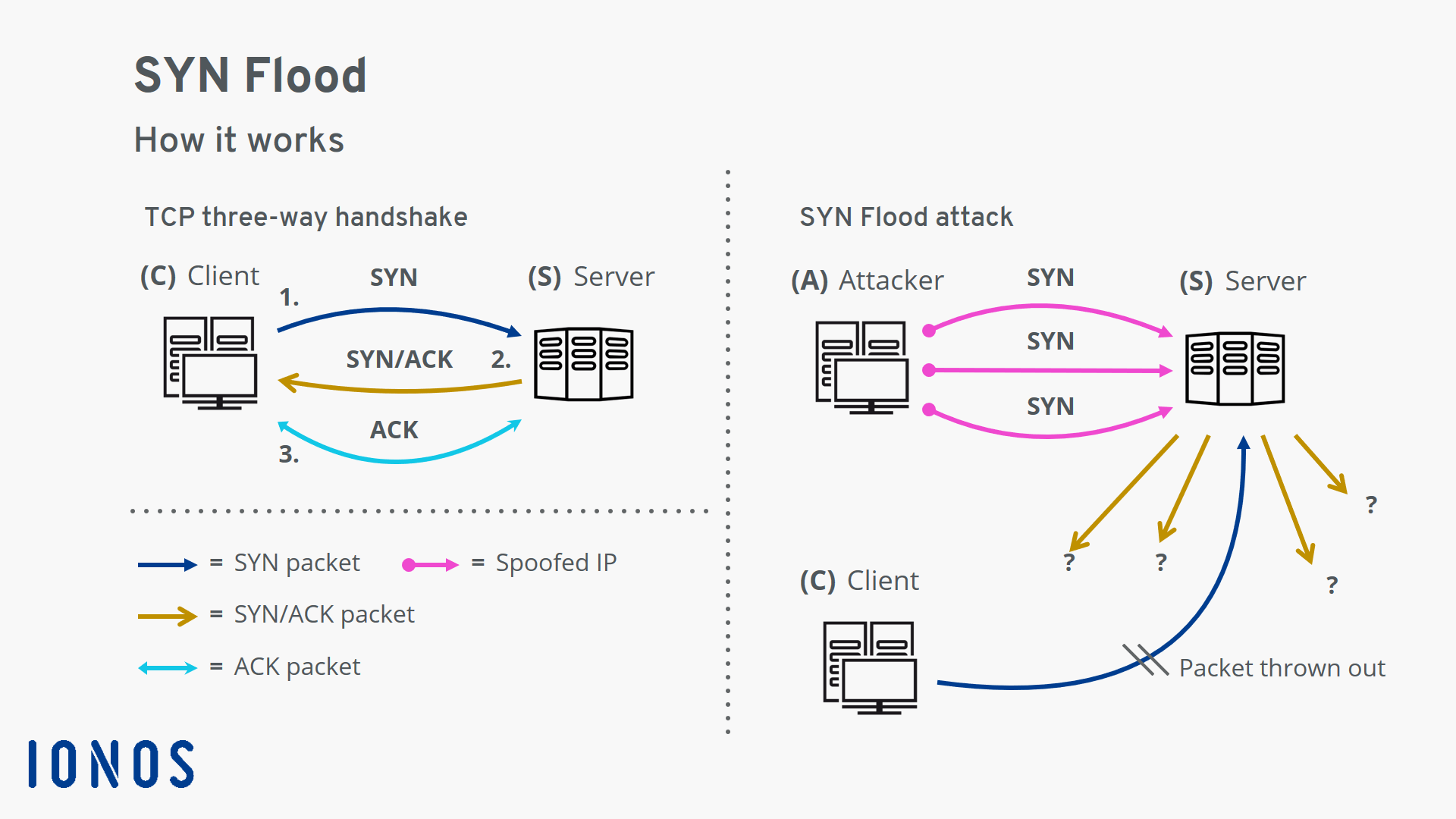
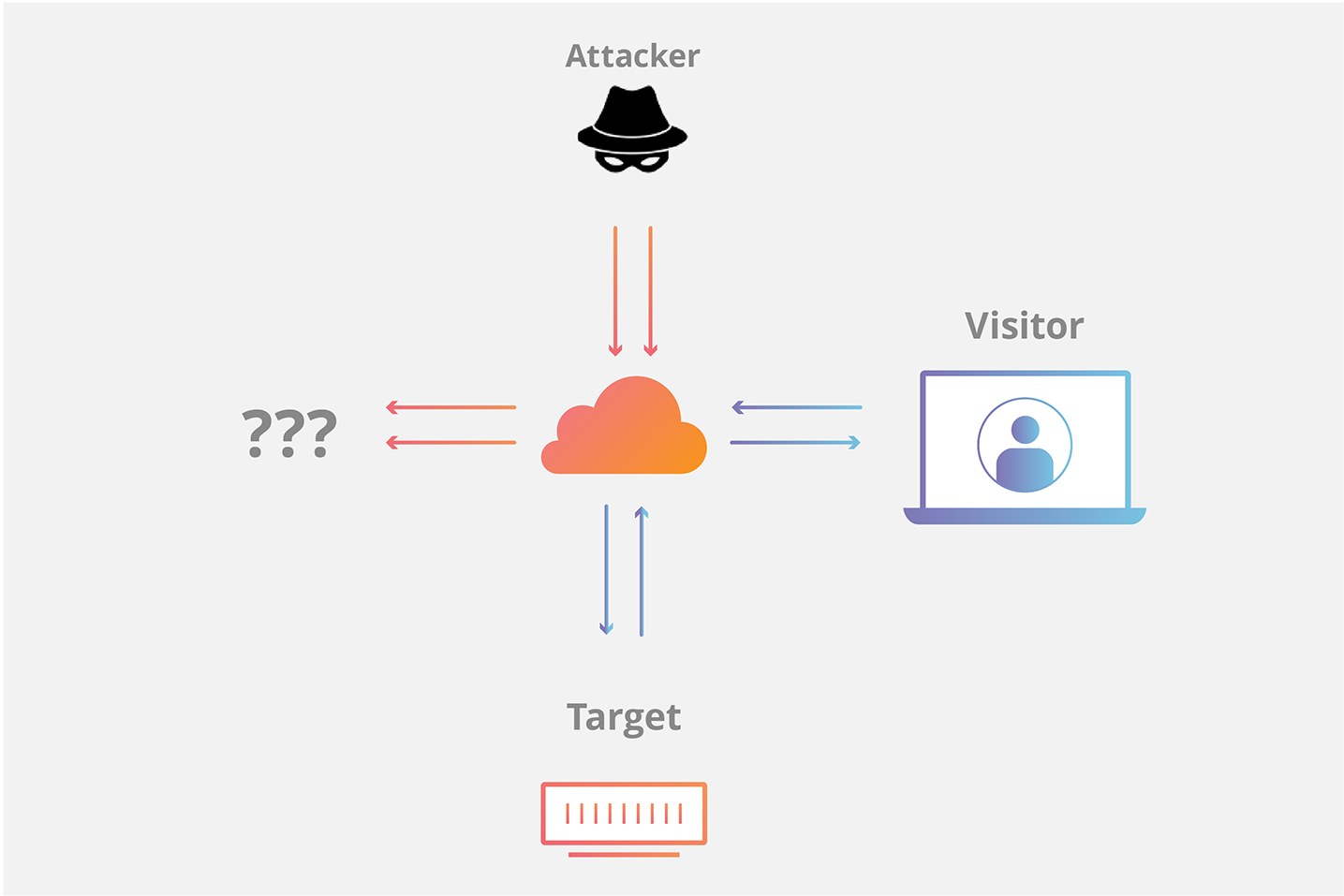
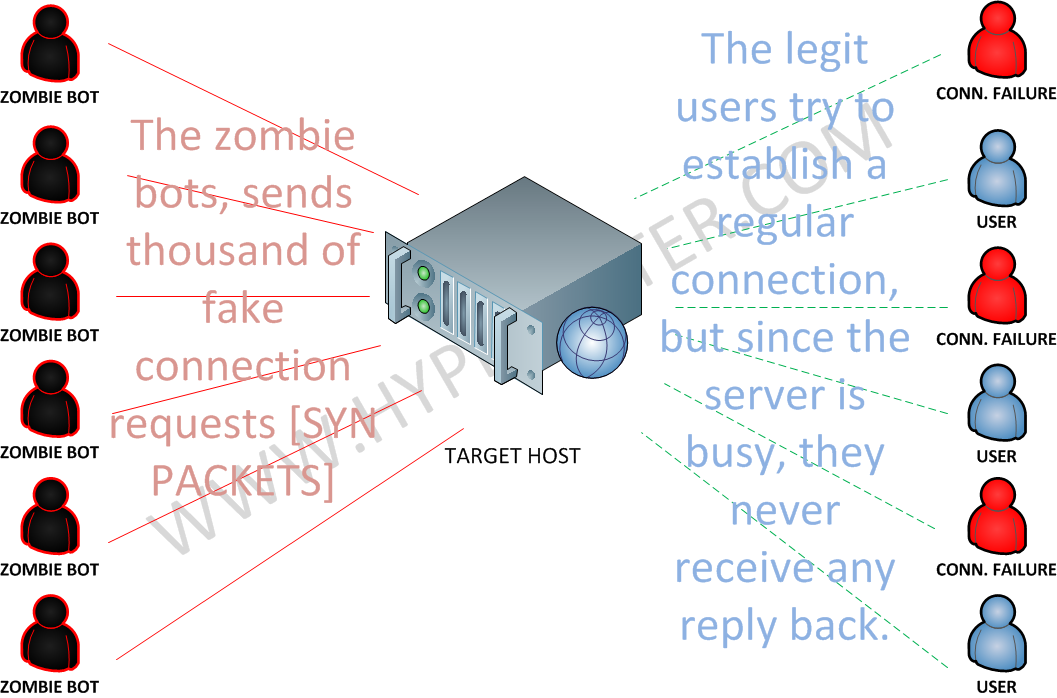
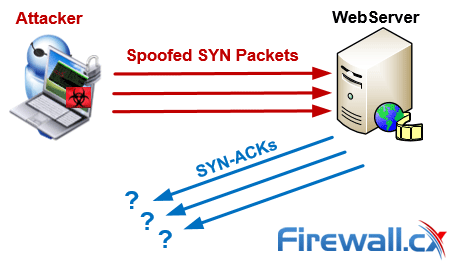
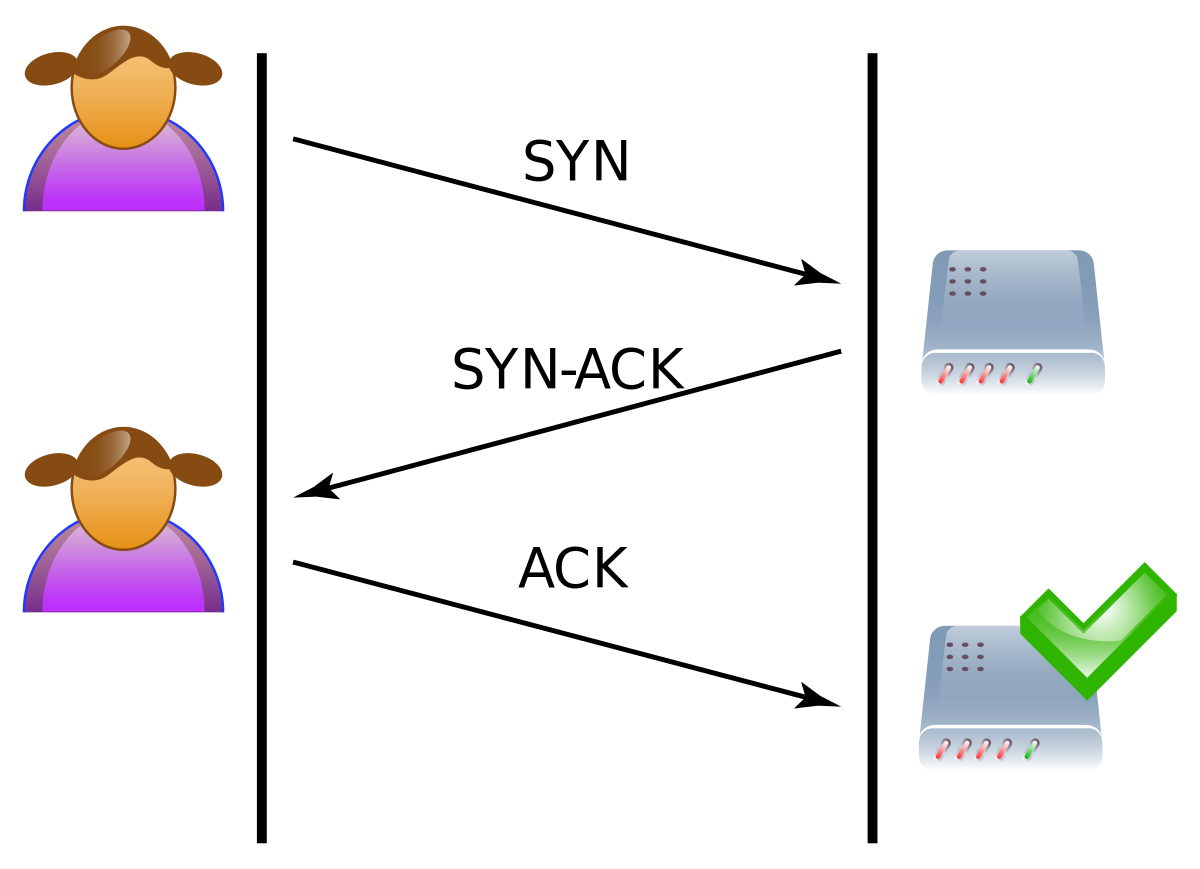
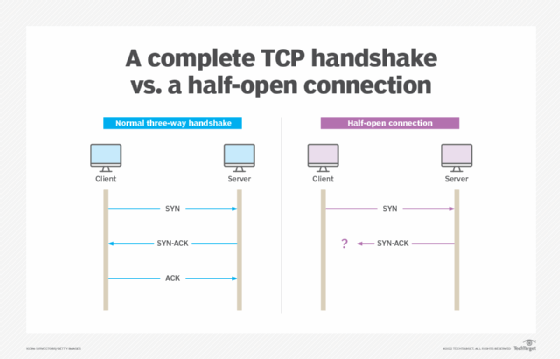
SYNGuard: Dynamic threshold‐based SYN flood attack detection and mitigation in software‐defined networks - Rahouti - 2021 - IET Networks - Wiley Online Library
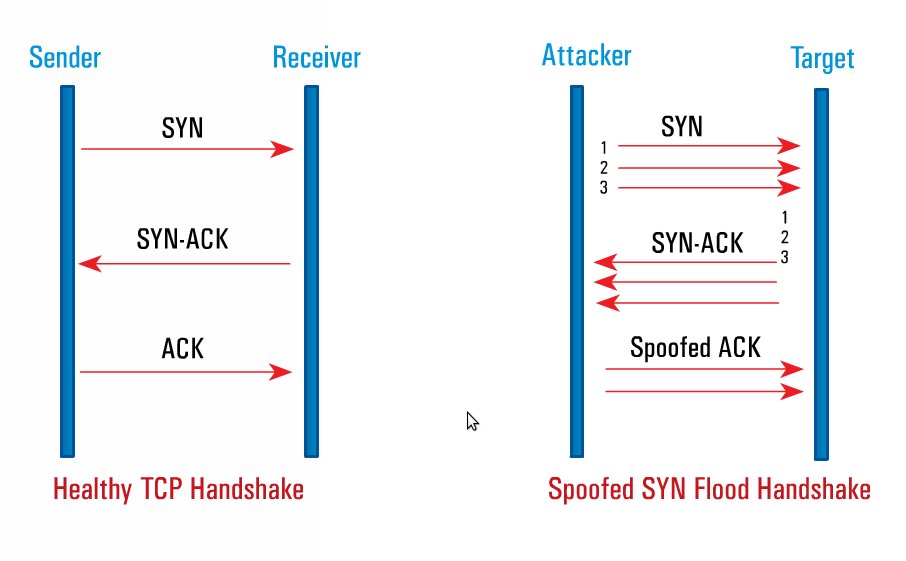
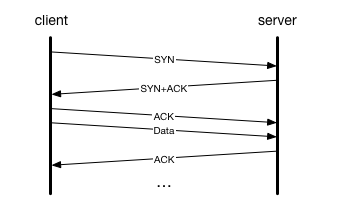
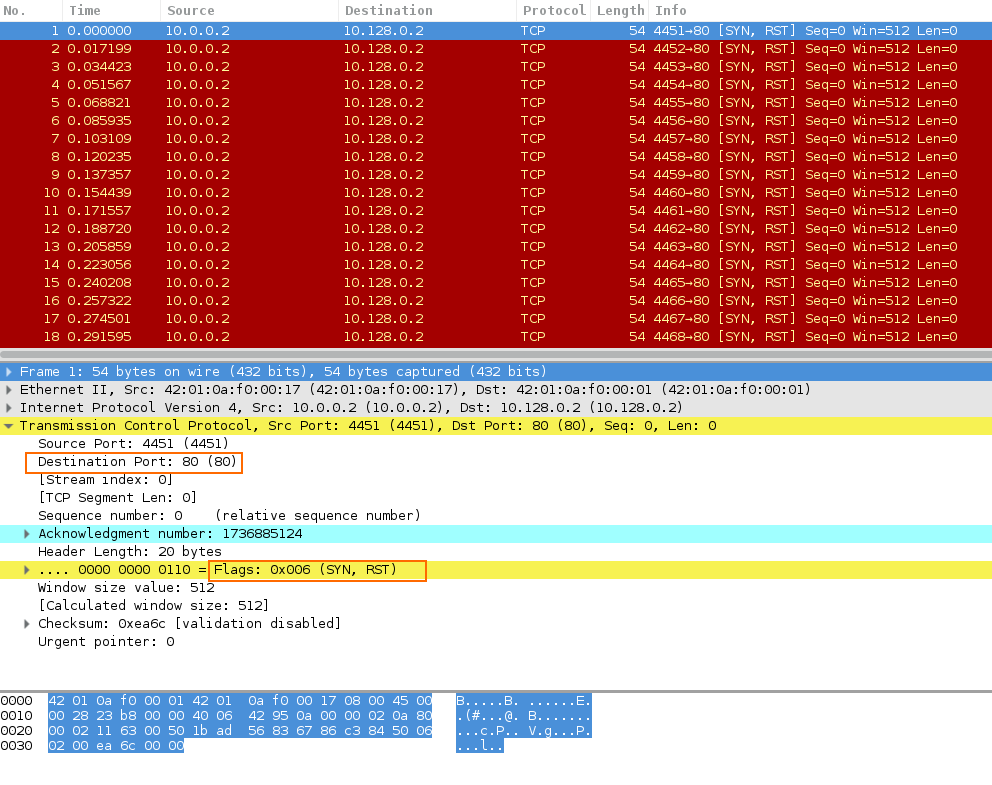
SYN-ACK-ACK proxy flood process. To initiate this attack on Juniper... | Download Scientific Diagram