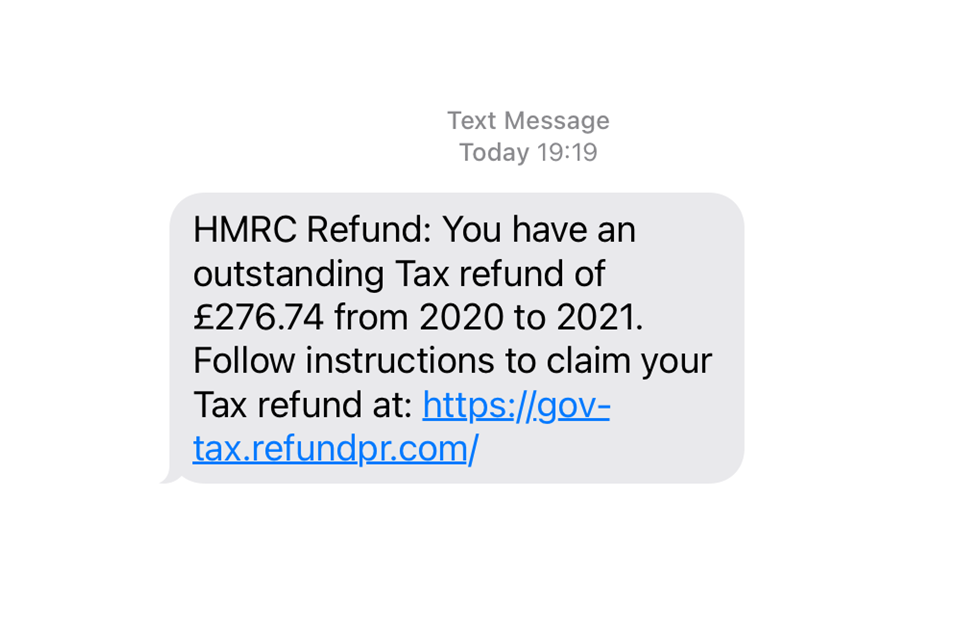
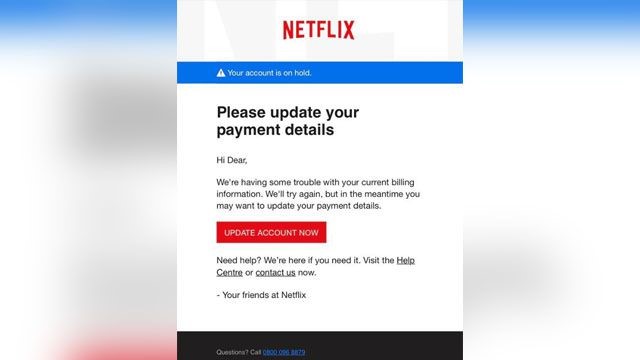
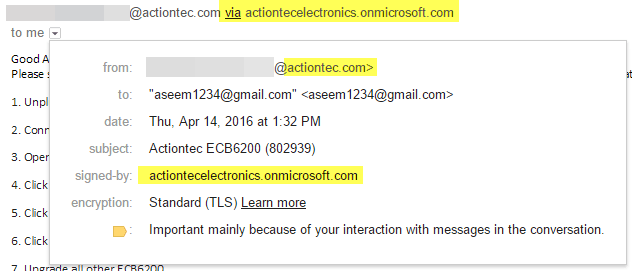
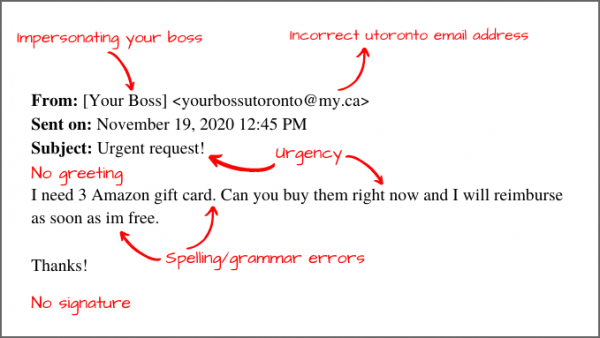
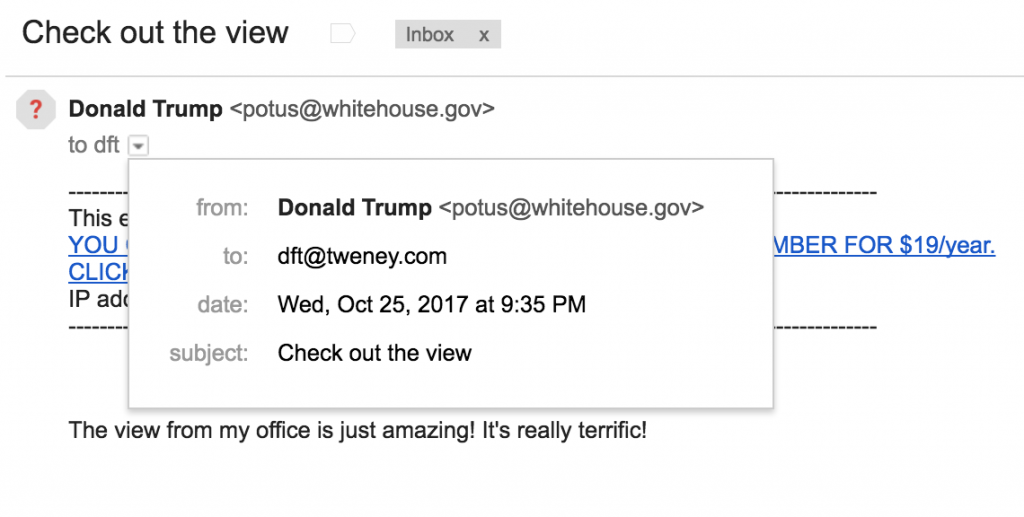
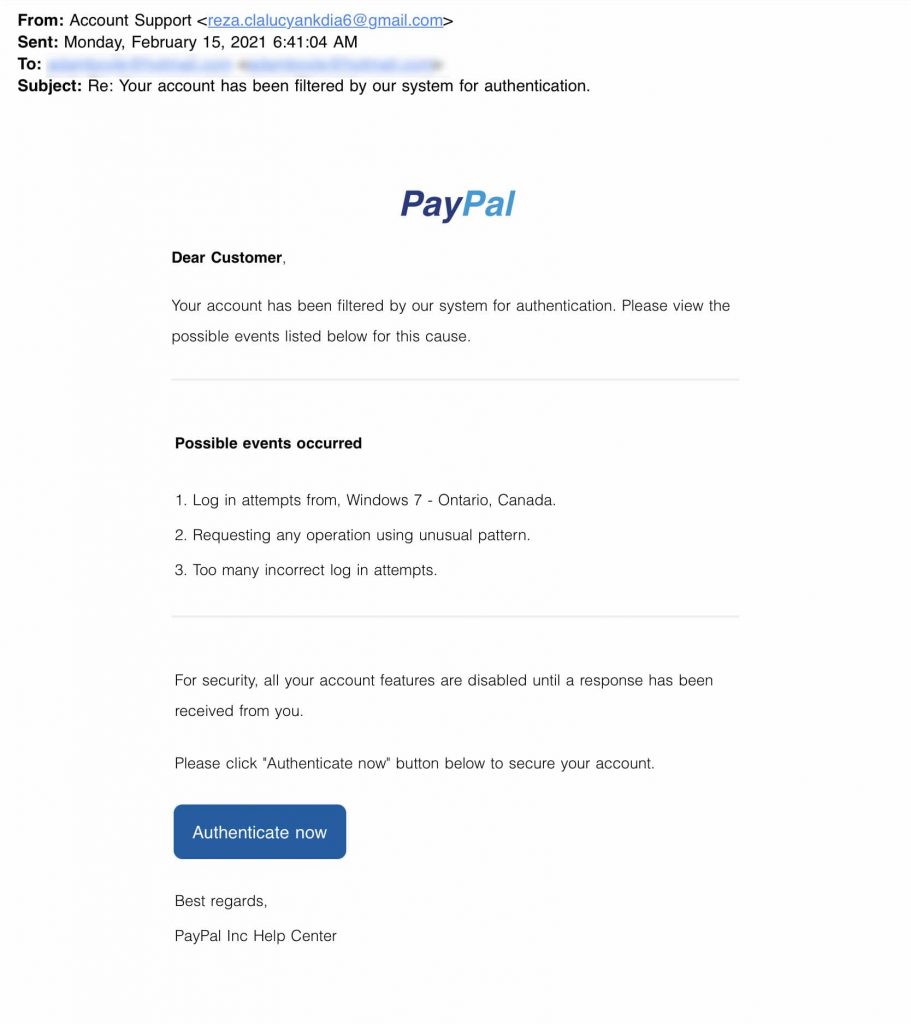
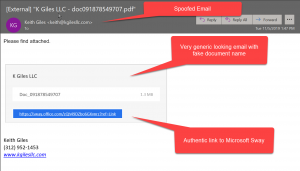
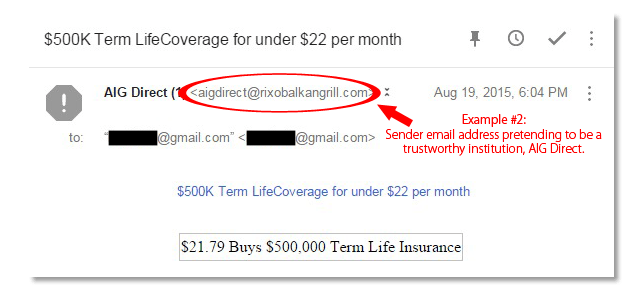
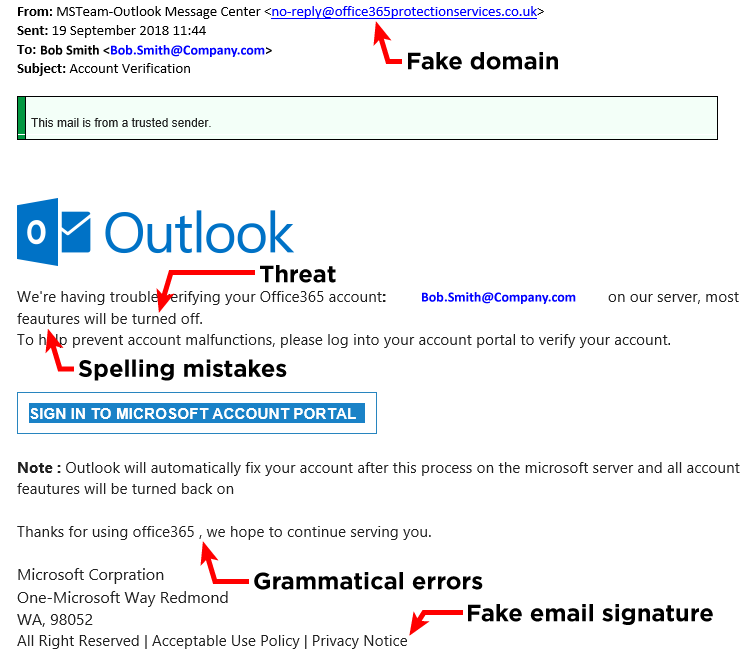
Phishing Alert: Payroll Notification Scam Links to Malicious Website | Information Technology | University of Pittsburgh

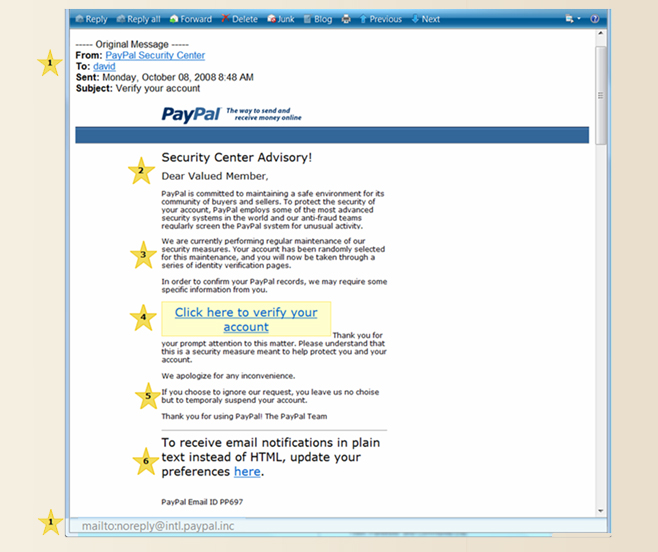
Email spoofing glyph icon. Illegitimate business. Forged sender. Online scam. Spamming. Fake email header. Mail phishing. Cybercrime. Silhouette symbol. Negative space. Vector isolated illustration Stock Vector | Adobe Stock

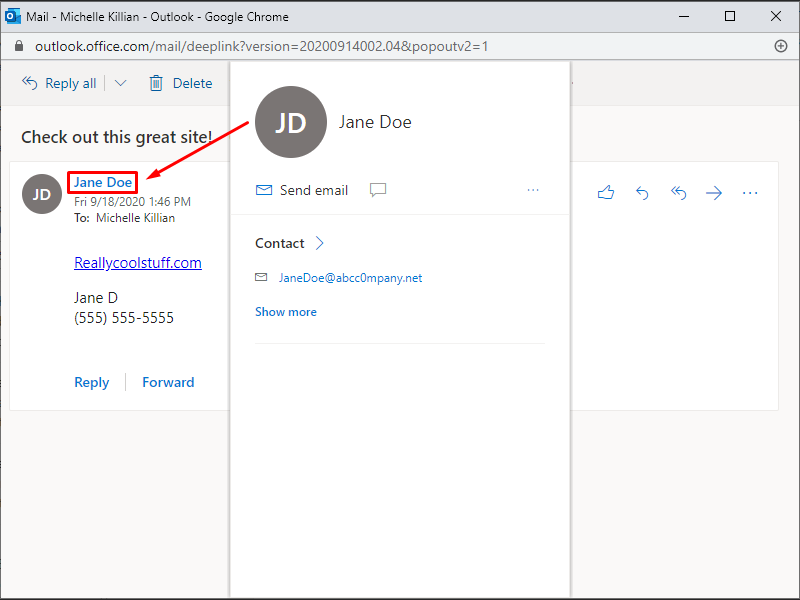
Phishing Alert: Fake Email Scam Mimics Pitt Passport Login Page | Information Technology | University of Pittsburgh
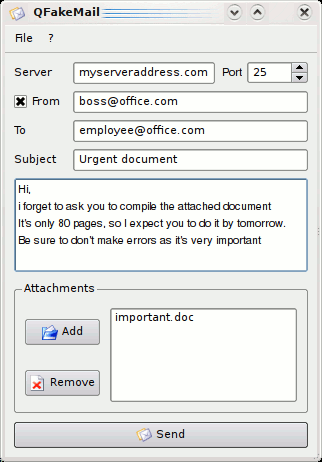
Email spoofing icon. Illegitimate business. Forged sender. Spamming. Fake email header. Mail phishing. Cybercrime. Flat design, linear and color style Stock Vector Image & Art - Alamy