Venkat Java Projects: - Java Ieee Projects List SN O Project Title Domain | PDF | Internet Of Things | Data Mining

Mathematics | Free Full-Text | State-Based Differential Privacy Verification and Enforcement for Probabilistic Automata

Soft Computing based object detection and tracking approaches: State-of-the-Art survey - ScienceDirect

Introducing scalable 1-bit full adders for designing quantum-dot cellular automata arithmetic circuits | springerprofessional.de

New Finite Automata Applications in Novice Program Comprehension: 9783330029057: Computer Science Books @ Amazon.com
Diverse examples of probabilistic automata, including the automaton... | Download Scientific Diagram
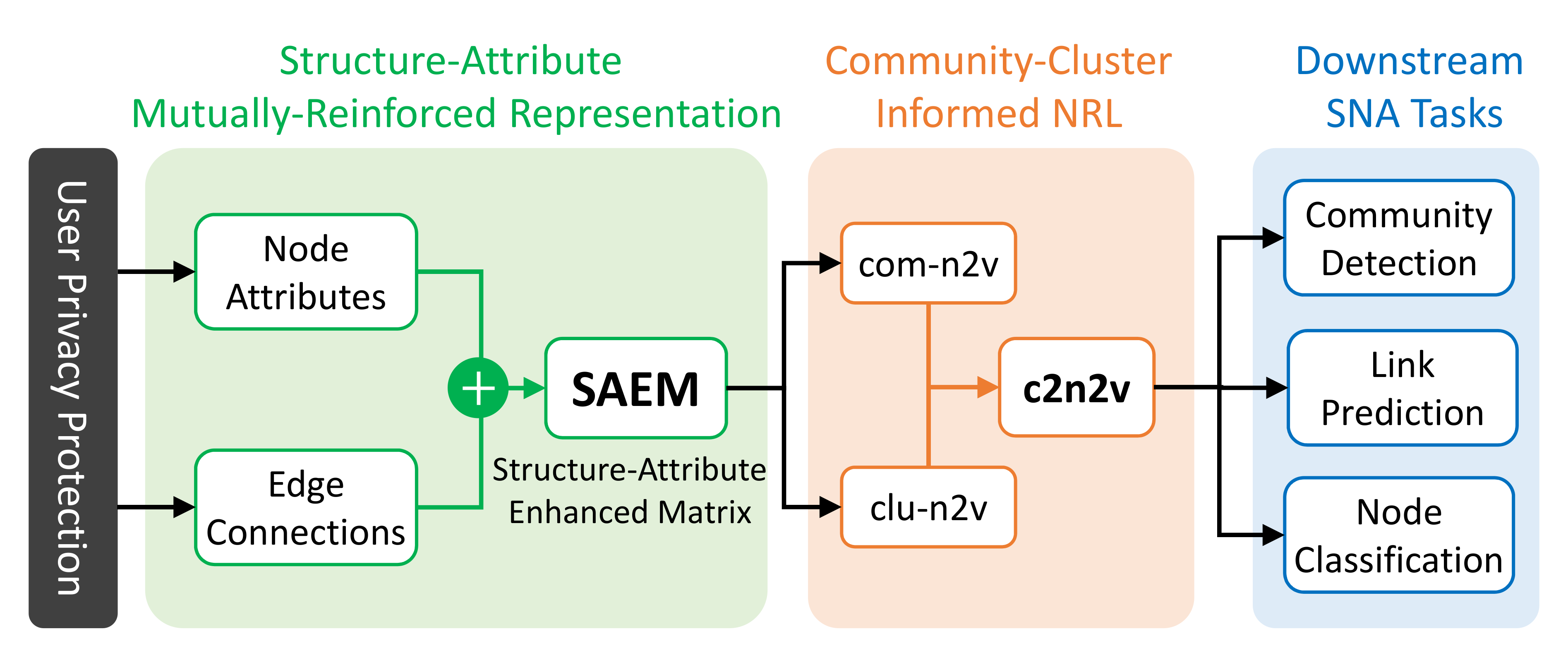
Applied Sciences | Free Full-Text | Learning Effective Feature Representation against User Privacy Protection on Social Networks
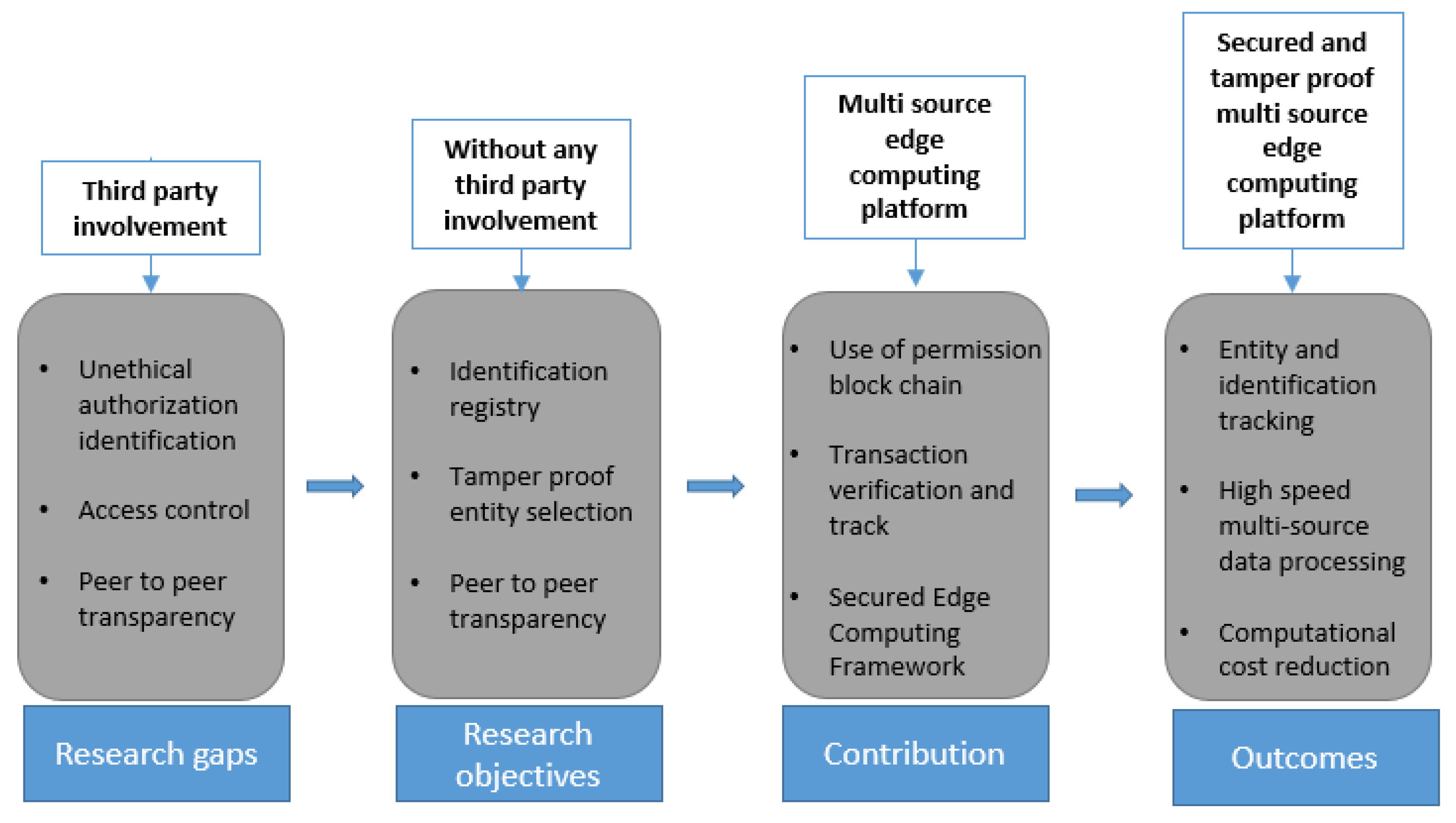
Sensors | Free Full-Text | BlockEdge: A Privacy-Aware Secured Edge Computing Framework Using Blockchain for Industry 4.0
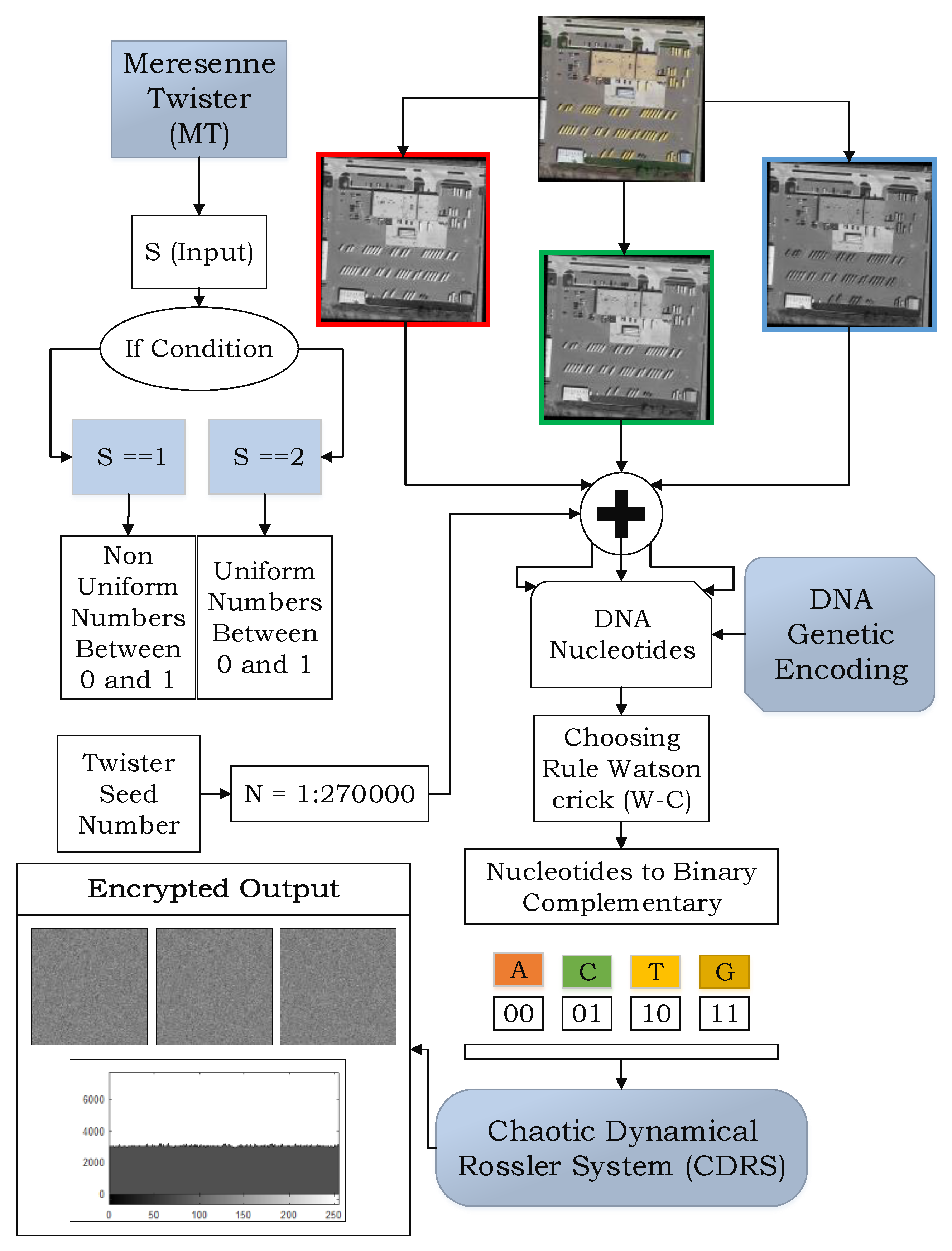
Remote Sensing | Free Full-Text | A Novel Privacy Approach of Digital Aerial Images Based on Mersenne Twister Method with DNA Genetic Encoding and Chaos
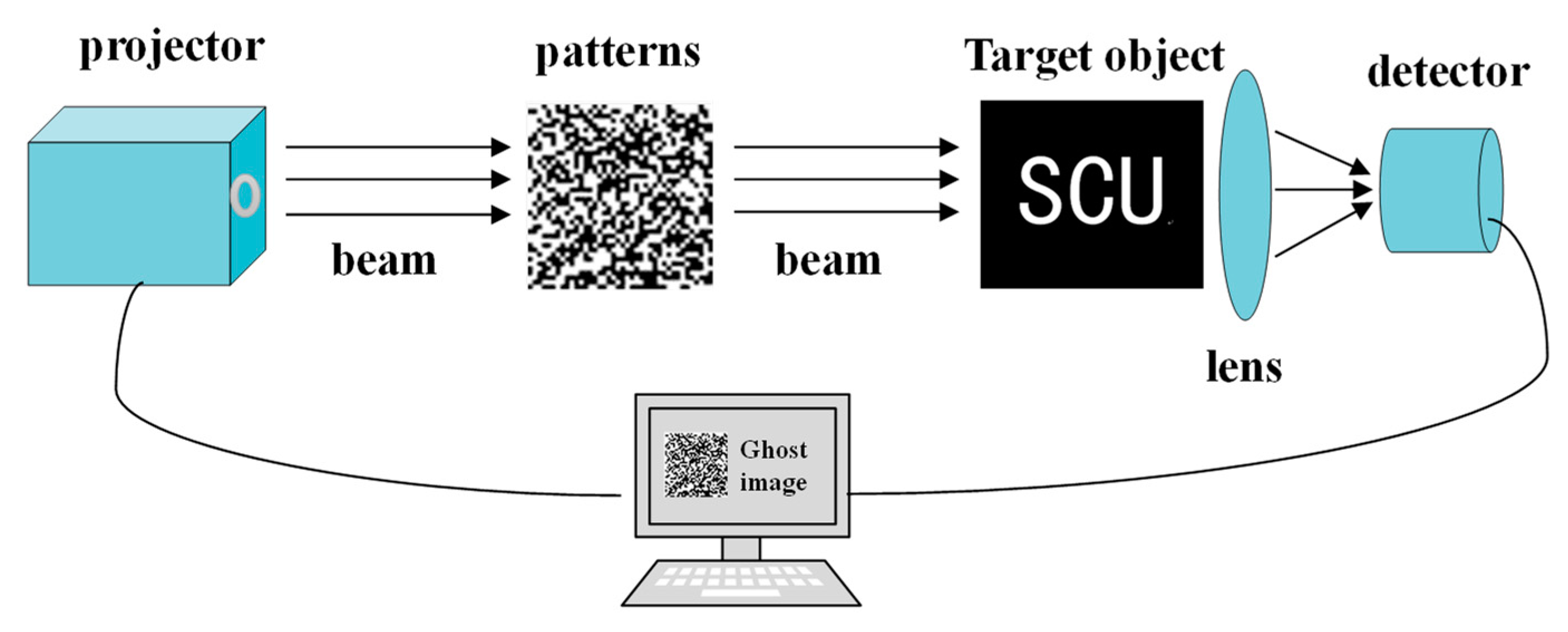
Symmetry | Free Full-Text | 3D Copyright Protection Based on Binarized Computational Ghost Imaging Encryption and Cellular Automata Transform
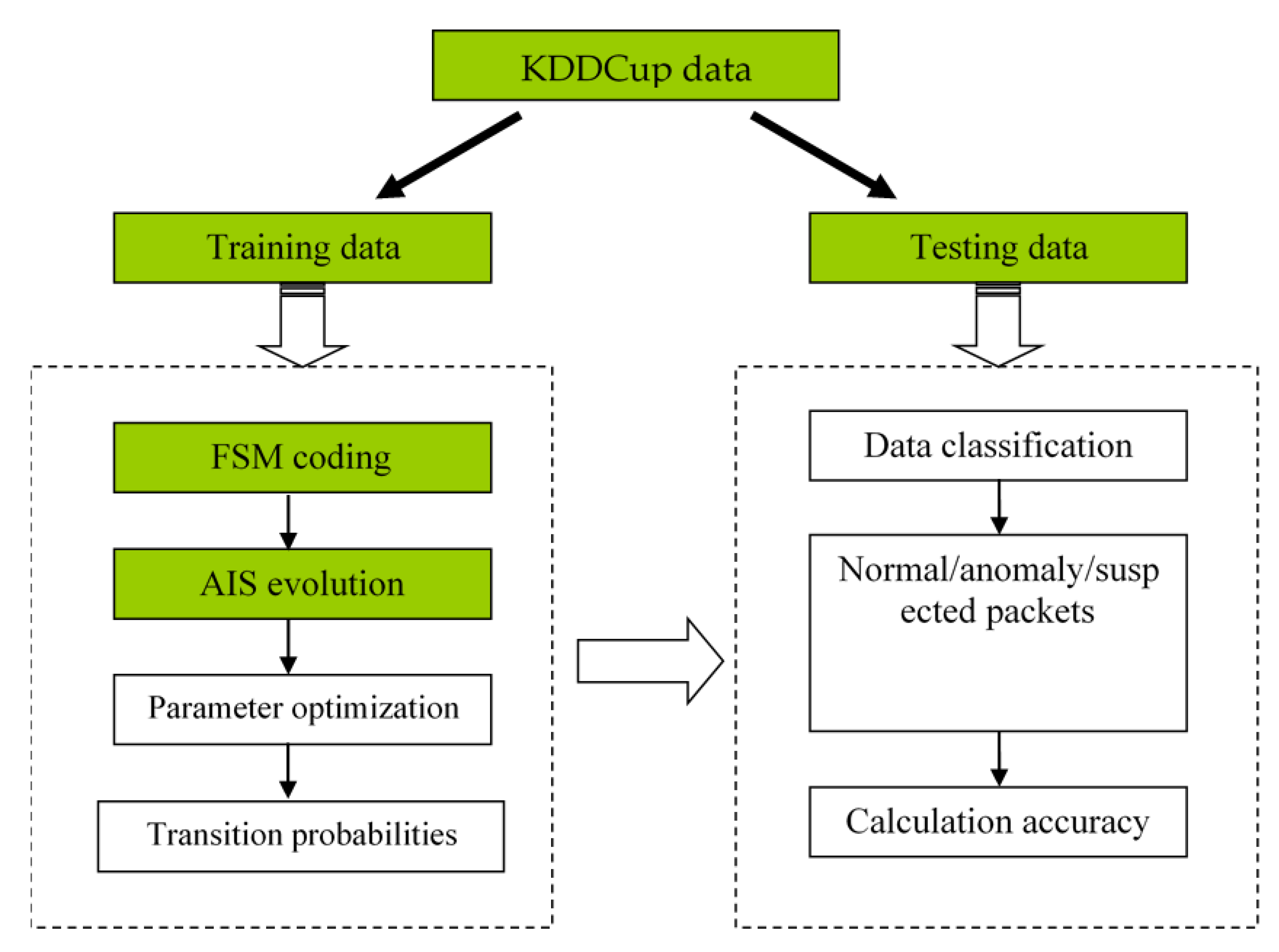
Applied Sciences | Free Full-Text | Detecting Mixed-Type Intrusion in High Adaptability Using Artificial Immune System and Parallelized Automata

A novel method for digital image copy-move forgery detection and localization using evolving cellular automata and local binary patterns | SpringerLink